Slepaya Zona (Слепая зона): Lynx and LockBit’s Blind Spot
12 Jan 2025
4 MIN read
How Windows Attributes Create an Unexpected Defence Against Modern Ransomware
Imagine uncovering a glaring blind spot in one of the most feared ransomware families in recent years—LockBit. What if a simple Windows feature could serve as the unexpected key to protecting your critical data?
Creating robust software is challenging. Even for criminal developers behind sophisticated ransomware, perfection is elusive. This is where Agger Labs steps in, revealing a breakthrough that transforms a minor oversight into a significant defensive advantage.
The Discovery: A Simple Attribute’s Powerful Impact
During routine analysis of Lynx and LockBit’s behaviour, our research team noticed something peculiar: files and folders marked with the “System” attribute remained untouched during encryption runs. This wasn’t a glitch or a one-off occurrence—it’s hardcoded into ransomware’s pre-infection file system enumeration process.
The implications are significant: by marking folders with the System attribute, organisations could potentially shield critical data from encryption. While relying solely on this defence may not be practical, it represents an intriguing opportunity for layered security.
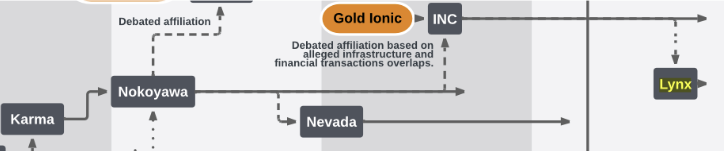
Lynx: A New Ransomware Player
First identified in July 2024, Lynx emerged as the successor to INC ransomware. Operated as a ransomware-as-a-service (RaaS) model, LYNX has actively targeted organisations across sectors such as retail, real estate, and financial services, primarily in the U.S. and U.K.
Sharing much of its source code with INC, Lynx is a testament to the evolution of ransomware—a phenomenon also observed in the infamous LockBit family.
LockBit’s Journey: From “ABCD” to 3.0
LockBit’s trajectory, beginning in 2019 as “ABCD,” demonstrates a relentless drive for innovation. Over its iterations, it has introduced advanced cryptographic techniques, refined operational tactics, and creative monetisation strategies. Today, LockBit 3.0 stands as one of the most sophisticated ransomware variants—but like Lynx, it has its flaws.
Hat tip to the epic work Orange Cyberdefense is doing in this space!

SYSTEM Attribute: The Unexpected Gatekeeper
In Windows systems, file attributes define behaviour and visibility for files or directories. The System attribute, typically reserved for essential OS files, creates an additional layer of protection:
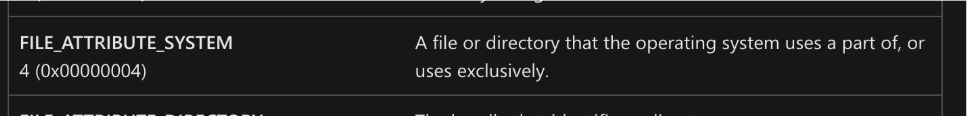
Files with the System attribute require extra steps to delete or modify, often involving specialised tools. These attributes are rarely applied to everyday file types targeted by ransomware (e.g., .docx, .pdf).
It is our hypothesis that those creating ransomware strains may avoid files marked as System to prevent accidental disruption of critical system operations. Notably, applying the System attribute on Windows 10/11 to user files or folders generally doesn’t affect usability, aside from minor prompts during modification.
The Blind Spot: How Ransomware Avoids System-Marked Objects
Let’s take Lynx as an example. Its logic actively skips files marked with the System attribute. In simplified terms:
- FindFileData.dwFileAttributes: This function checks whether a file is marked as a system file.
- If the FILE_ATTRIBUTE_SYSTEM bit is set, the ransomware bypasses the file entirely, much like avoiding a “Do Not Enter” sign.
For LockBit, this oversight is even more dramatic—folders marked with the System attribute halt further processing entirely. A single command like attrib +s c:\Users could have wide-reaching defensive effects. - The below code is part of LYNX mw_enumDir procedure – the code checks if the FILE_ATTRIBUTE_SYSTEM bit (0x4) is set. If (FindFileData.dwFileAttributes & 4) == 0, the file is not a system file, and the code inside this if block executes else jump to LABEL_65.
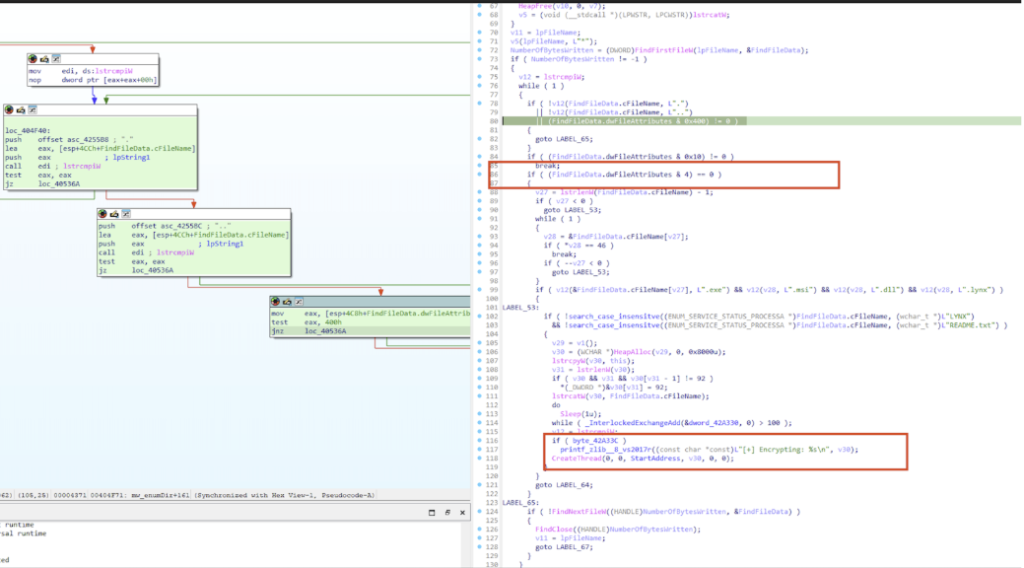
Sample: 9A47AB27D50DF1FABA1DC5777BDCFFF576524424BC4A3364D33267BBCF8A3896
The following ransomware families exhibit similar behaviour:
- LockBit 2/3
- Lynx and INC
- Cuba
- Avaddon
- Blackout: Written in C#, Blackout ransomware encounters an UnauthorizedAccessException when attempting to modify files with the System or ReadOnly attributes. With its empty exception handler, the ransomware simply skips these files, leaving them untouched.
Leveraging the Flaw: Practical Defence Strategies
While this discovery is promising, it’s not a silver bullet. Attribute-based defence won’t stop LYNX or LockBit entirely, and future versions are likely to patch this oversight. However, using this as part of a defense-in-depth strategy—alongside strong backups, access controls, and continuous monitoring—can buy critical time during an incident.For example, a simple command like the following could protect sensitive directories: attrib +s c:\CriticalData | attrib +s c:\CriticalData\*
Conclusion
Avoiding System-marked files/folders highlights the potential for understanding malware’s self-imposed limitations. However, attackers adapt quickly, and future versions of LockBit and Lynx may address this flaw.Organisations should view this as a temporary advantage and integrate it into broader security practices. The key takeaway? Defence-in-depth strategies, coupled with insights like this, provide resilience against ever-evolving threats. This unexpected oversight in ransomware logic offers defenders a rare opportunity to outmanoeuvre their adversaries. By leveraging the System attribute, organisations can protect critical assets and gain precious time to respond to ransomware attacks.
Yet, caution remains essential. Criminal groups evolve rapidly, and today’s blind spot could become tomorrow’s feature. Agger Labs is here to help you stay one step ahead.
Ready to turn this discovery into action? Let’s safeguard your future together.