NSA shares guidance on zero-trust implementation to counter adversaries in networks
7 Mar 2024
2 MIN read
source: National Security Agency
The National Security Agency (NSA) has issued new guidance aimed at assisting organizations in reducing an adversary’s ability to move laterally within their internal networks by implementing the principles of a zero-trust framework.
A zero-trust security architecture enforces stringent access controls to network resources, regardless of their location relative to the organization’s physical boundaries, thereby diminishing the repercussions of a security breach.
This model starkly contrasts with conventional IT security paradigms that assume entities within the network are trustworthy, instead operating under the assumption that threats are already present and restricting internal network access accordingly.
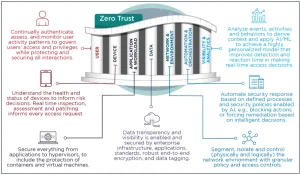
The journey towards achieving zero-trust maturity involves addressing several key elements, or pillars, which adversaries could exploit during an attack.
Today, the NSA unveiled guidance focused on the network and environmental component of zero-trust, which includes all digital and physical assets, user accounts, and communication protocols within an organization.
Under zero-trust, network security is enhanced through strategies such as data flow mapping, macro and micro-segmentation, and the use of software-defined networking, each requiring organizations to attain certain maturity levels to effectively implement zero-trust principles.
The NSA’s guidance specifies that the network and environment pillar serves to safeguard critical resources by managing network access, controlling data flows, segregating applications and workloads, and employing end-to-end encryption.
Data flow mapping involves cataloging the storage and processing locations of data. An organization reaches advanced maturity in this area by maintaining comprehensive inventories and visibility of data flows and addressing any new or unusual data pathways.
Macro-segmentation restricts an attacker’s lateral movement across the network by dividing it into segments based on departmental functions. This approach ensures that access to network segments is strictly need-based, thereby narrowing potential avenues for attack.
Micro-segmentation further divides network management and applies strict access policies to minimize lateral data movement, with the NSA highlighting the role of micro-segmentation in isolating users, applications, or workflows to minimize attack surfaces and breach impacts.
Software-defined networking enhances micro-segmentation by offering customized security monitoring and alerts and facilitating policy enforcement across all network segments from a centralized platform.
The NSA outlines four levels of maturity for the network and environment pillar, ranging from initial preparation to advanced stages where comprehensive controls and systems are in place for optimal network visibility, monitoring, and scalability.
Building a zero-trust architecture is an intricate process that progresses through these maturity stages to create a robust enterprise framework capable of detecting, resisting, and responding to threats.
The NSA’s first zero-trust framework guide was published in February 2021, detailing the model and its benefits. In April 2023, the agency provided additional guidance on achieving user pillar maturity within the zero-trust framework.